
This weekend I received an upset call from my Mom. She got an email from Amazon claiming that a hold was being placed on all her pending orders. At 70 years old, she gets some essential items delivered regularly through Amazon, which saves her from having to go to some otherwise potentially dangerous places during this pandemic.
 Fortunately, she also has a son who explained to her the dangers of Phishing emails. That’s me, by the way—my brother stays as far off the grid as he can manage. Before I had a chance to ask, she stated, “Don’t worry, I didn’t click on anything,” and asked me if I could take a look at the email, just to make sure. Beaming with pride, I asked her to send it over to me.
Fortunately, she also has a son who explained to her the dangers of Phishing emails. That’s me, by the way—my brother stays as far off the grid as he can manage. Before I had a chance to ask, she stated, “Don’t worry, I didn’t click on anything,” and asked me if I could take a look at the email, just to make sure. Beaming with pride, I asked her to send it over to me.
At first glance, I could see the reason for her concern. The email looked legit. But it wasn’t.
Alleviating her concerns, I explained that the email was fake and why. Hearing the relief in her voice felt good. But after we hung up, I stared at that email for a bit, feeling myself getting angrier. These hackers targeted my Mom.
Expletives flew, but ultimately, there wasn’t much I could do about it. Unless.
It occurred to me that these hackers pay for email addresses. They pay for the software used to create the fake emails. They are spending time and money in their efforts to scam people, so the more people I can help to not fall for these scams, the more it costs them.
As revenge goes, it’s not exactly Liam Neeson hunting down hackers and making them pay, but then, I don’t have that particular skill set. So let’s discuss Phishing emails and how to spot them.
 What is Phishing?
What is Phishing?
Before we can talk about how to avoid Phishing, we need to understand it. Much like one would buy tools to go out fishing, Hackers do the same. Instead of fishing poles, they are buying email addresses. Rather than baiting hooks with worms, they craft convincing emails with fake links. From there, it’s just a matter of casting the bait and seeing who clicks on it.
It really is just like fishing. The simplicity of it is the reason that they can target so many people. And the worst part is that it works—many of the email addresses they purchase come from successful phishing attacks. But they want a lot more than email addresses.
Phishing scams very often target specific systems. They try to get social media usernames and passwords, access to Netflix, Amazon, and Apple accounts, financial information, business data. If any value can be drawn from the account, they want it.
And on the dark web, every piece of personal data has a dollar value. Advertisers want it to sell to you, and criminals want it to steal from you.
There is no such thing as not being important enough. Hackers can make money on every piece of information they can get about you. That’s why the Phishing scams will never end, but you can protect yourself.
Avoid Getting Phished!
It’s no secret that the people who most often get phished are either Unaware, Busy, or Lazy. All Phishing emails target people in these groups equally because Phishing emails rely on deception. If you’re reading this blog, we’re making you Aware. From here, it’s up to you.
If you’re paying attention, there are five clues that will help you to determine if the email is real or fake.
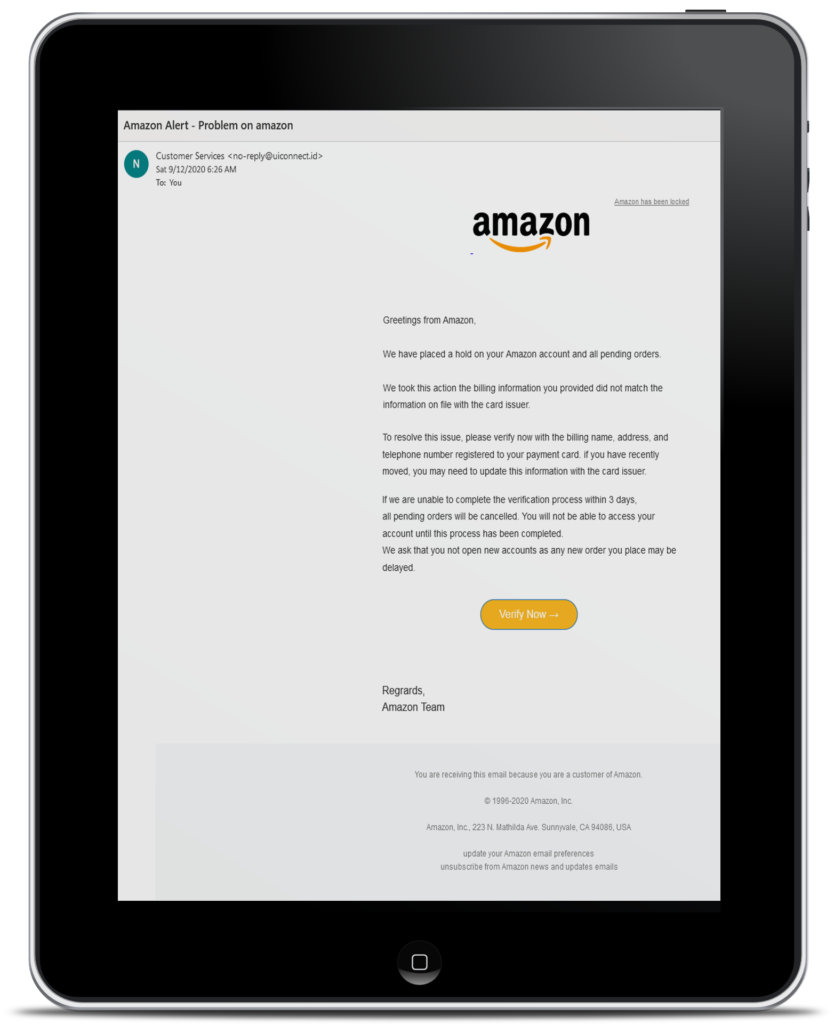
- Manufactured Sense of Urgency. Of all the things that go into a Phishing email, this is by far the most nefarious. As in the example with my Mom, the hackers are trying to make you act before you have a chance to think about it. This is where they get people more often than not. When it comes to email, no matter how urgent it seems, stop and look before you click.
2. Look at the Email Address. This is the primary giveaway of phishing emails. They can use the corporate logos and colors to dress up the emails all they want, but they can’t use the corporate domain names. If you get an email that claims it comes from Amazon and the sender’s address is moc.nozana@ ton it is fake. The same can be said for any company or government agency.

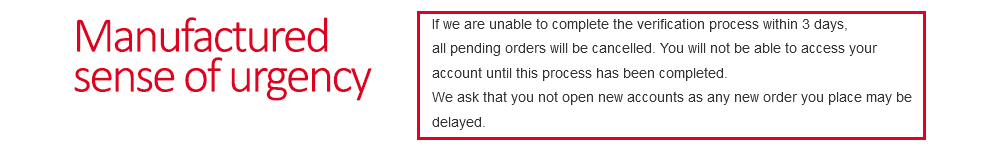
3. Read the Content of the Message. Most hackers are not native English speakers; as such, while they use spell checkers to make sure the words are correct, their sentence structure is rarely accurate. All companies and government agencies hire professionals to proof emails before they go out. While the occasional mistake might sneak through, odd phrases and blatantly grammatical errors are obvious indicators. Sometimes though, you have to pay close attention, in point 2. above, did you notice that I spelled it @anazon.com instead of @amazon.com. Don’t let the little things get past you.
4. Beware Link Buttons. We see them everywhere—on our smartphones, tablets, and most website. Buttons are very common, and we have been trained to use them. Hackers know this, so almost every Phishing email is going to have some type of button for you to click, with the words “click here” close by. The problem is that these buttons can link to anywhere. Most often, they go to malicious sites that have login boxes created to look just like the home page of the company used in the Phishing email. Once you put in your user name and password, they have your credentials. The rule of thumb is to never click on button links in your email—always manually go to the website and login. If there is an actual problem, that is the best way to find out.

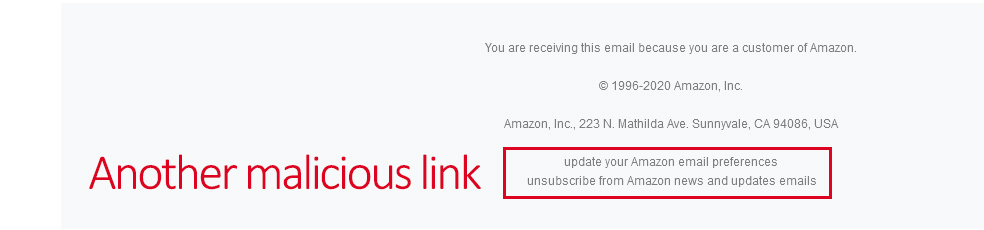
5. Tricky Links and Attachments. First off, no legitimate organization is going to send you unsolicited material. If you weren’t expecting a PDF or document from a company or government agency, it’s probably fake. Just opening these could infect your phone or computer. Also, beware of the unsubscribe and other links in these emails. Hackers are getting more sophisticated. They know that people are tired of getting daily advertisements, so they send out emails specifically to get you to click on the unsubscribe and other links. If they can’t trick you into logging into a site, they might be able to trick you into
revealing additional information.
Remember, with every success and failure, the hackers are learning, and their attacks are getting more advanced. But we can beat them by paying attention to our emails and not falling for their deceptions.
 Author: Chuck Sperati
Author: Chuck Sperati
After 25+ years in enterprise level IT, working as a tier I-III technician, trainer, technical writer, manager, compliance officer, and security specialist, Chuck left the corporate world last year to join Clark Computer Services. A managed services provider in Frederick, MD specializing in small business and residential clients, CLARK has a stellar 5-Star Reputation, making customer service their highest priority. Also a published author, Chuck writes biweekly IT blogs covering a wide range of IT topics available at https://clarkcomputerservices.com/the-clark-report/
Further Reading

Halloween Safety: Be Ready When the Little Goblins Come Out
It's a night full of treats for both kids and adults in Hagerstown. But a number of factors - including lots of people walking in the dark, the...

How to Clean & Disinfect Your Building
Having a clean space for employees to work in, and for visitors to be in, is part of your responsibility when you run and organization. Many large...
